ARTICLES
Encryption Export Compliance for iOS apps
Disclaimer: I am not a lawyer. This is not legal advice, this is for information purposes only. Consult an attorney for legal guidance.
If your iOS app is simply using ATS or HTTPS to communicate with an external server then your app is using Encryption. As such you may need to submit a year-end self classification report to the US government. This is far-reaching as Apple is pushing to require ATS in all apps. The original deadline was Jan 1, 2017, however it has been extended indefinitely. These requirements would include simple apps that may be using an external SDK with ATS enabled for metrics or advertising such as Facebook SDKs, Fabric, Crashlytics, Kitemetrics, etc.
While the self classification report doesn’t seem that hard to submit, finding out if you qualify and the instructions to submit it are a little challenging. For convenience I’ll post my research on finding those instructions here and link out appropriately.
A really good resource is the FAQ on iTunes Connect on Managing Your Apps Export Compliance. It answers questions such as “Does my app require an export compliance review if I only distribute it on the App Store in the U.S. and Canada?” Short answer, No. However, if you don’t live in the U.S. you are still subject to U.S. export laws since the app is uploaded to U.S. servers, even if you only publish your app in your home country.
In iTunes connect it asks you to fill out Export Compliance Information.
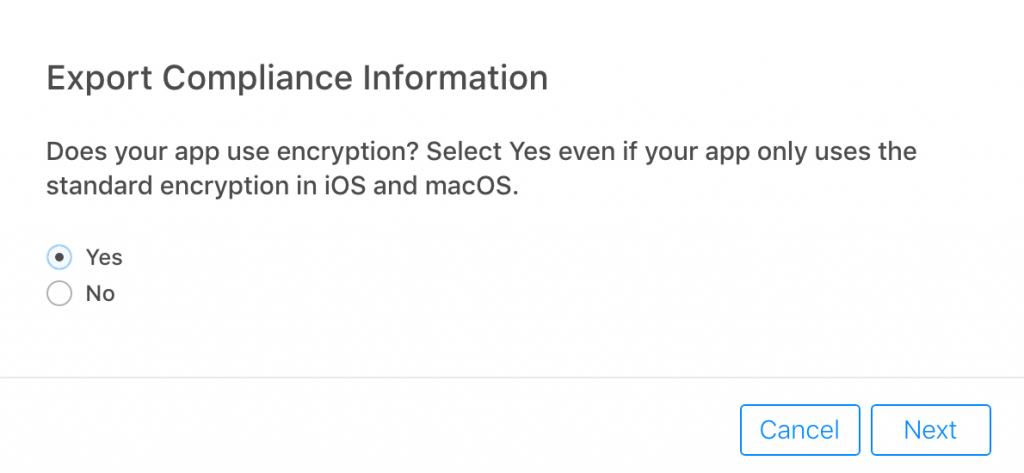
The first question is “Does your app use encryption? Select Yes even if your app only uses the standard encryption in iOS and macOS.”.
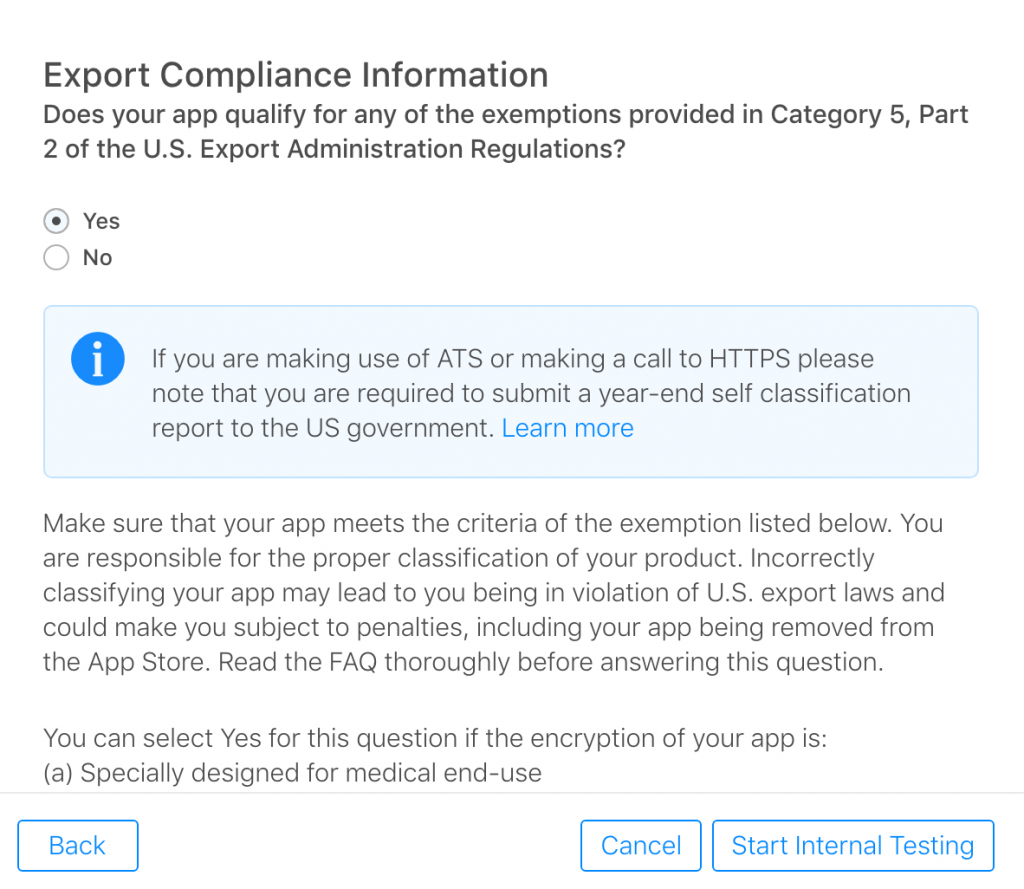
The second question is “Does your app qualify for any of the exemptions provided in Category 5, Part 2 of the U.S. Export Administration Regulations?”
If you answer yes it has the following info callout “If you are making use of ATS or making a call to HTTPS please note that you are required to submit a year-end self classification report to the US government.” This link on Encryption and Export Administration Regulations (EAR) as well as the FAQ are very instructive in learning more about the process.
The full text states:
Make sure that your app meets the criteria of the exemption listed below. You are responsible for the proper classification of your product. Incorrectly classifying your app may lead to you being in violation of U.S. export laws and could make you subject to penalties, including your app being removed from the App Store. Read the FAQ thoroughly before answering this question.
You can select Yes for this question if the encryption of your app is:
(a) Specially designed for medical end-use
(b) Limited to intellectual property and copyright protection
(c) Limited to authentication, digital signature, or the decryption of data or files
(d) Specially designed and limited for banking use or “money transactions”; or
(e) Limited to “fixed” data compression or coding techniquesYou can also select Yes if your app meets the descriptions provided in Note 4 for Category 5, Part 2 of the U.S. Export Administration Regulations.
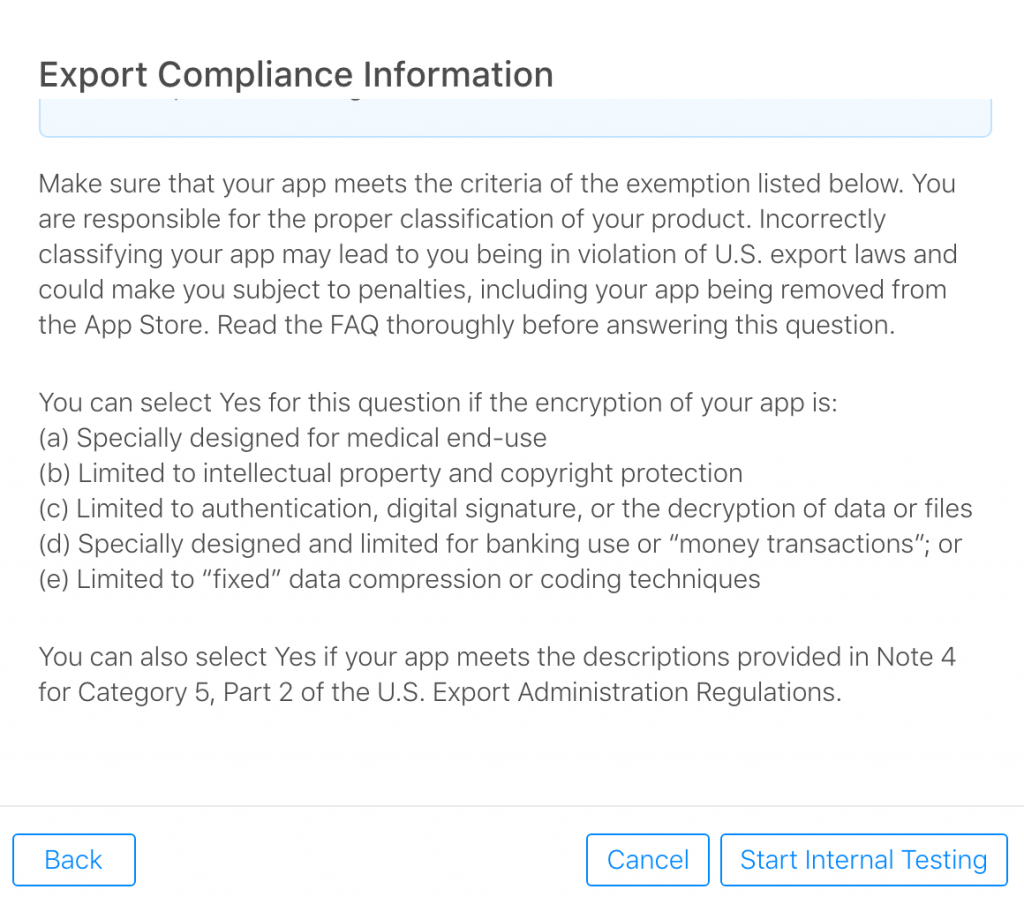
The exemption list shown only lists 5 categories. However, you should read Note 4 as it contains more descriptions. Here is link to the full contents of Note 4
Ok. Hopefully by now you or your lawyer have determined if your app qualifies for an exemption or not. If so and you determine that you also need to submit a year-end self classification report you’ll need to find out how to do that as well. Basically you fill out 12 columns in a .csv file and email it to [email protected] and [email protected] no later than February 1.
Here are some links with instructions on how to file:
How to file along with how to create the .CSV and some Examples
Supplement No. 8 to Part 742—Self-Classification Report for Encryption Items
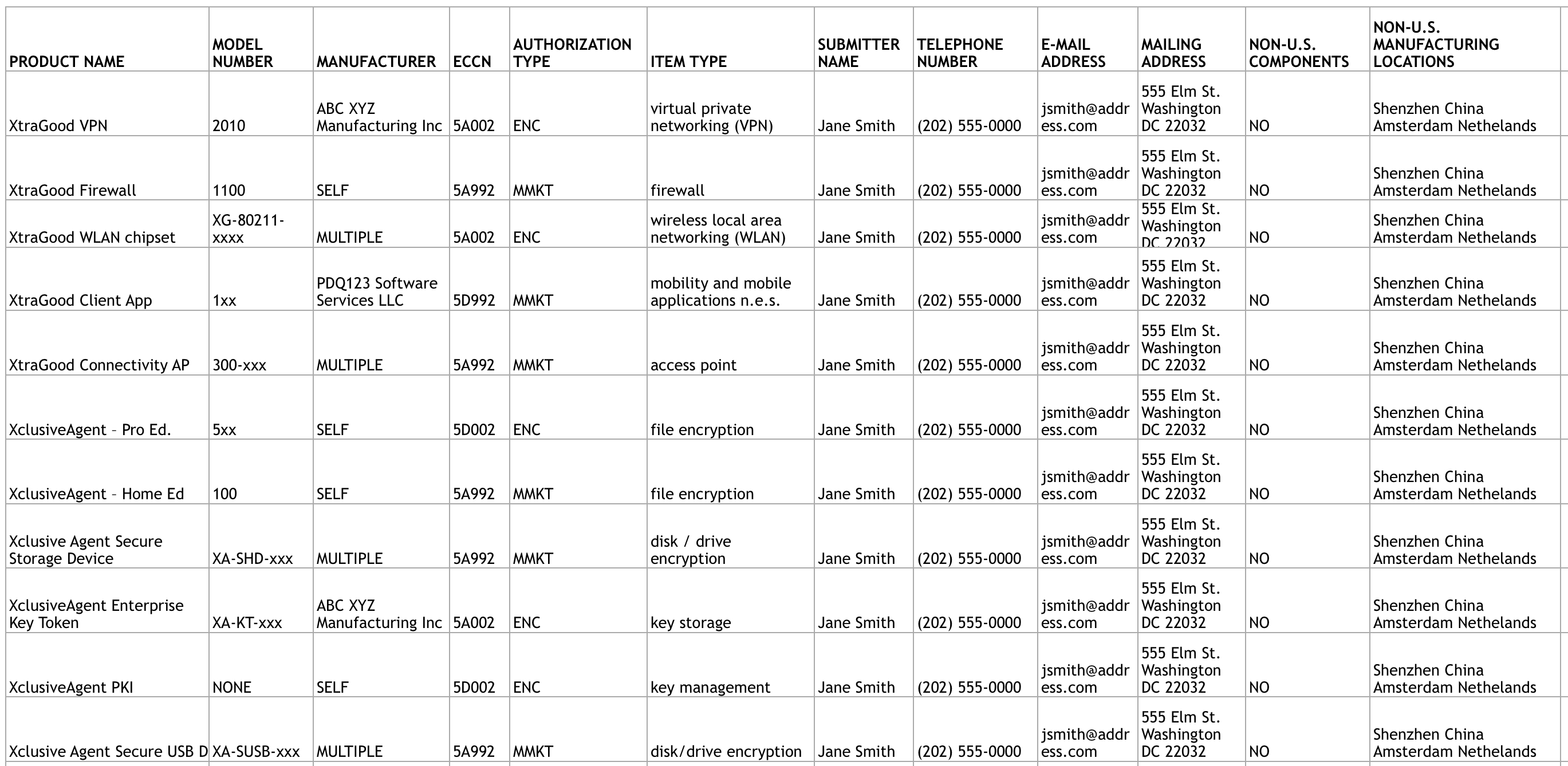
Below is a screenshot of one of the example files:
For some iOS apps distributed via the App Store it would seem that the following fields could be filled out as:
ECCN: 5A002 or 5A992
AUTHORIZATION TYPE: MMKT
ITEM TYPE: Mobility and mobile applications n.e.s.
NON-U.S. COMPONENTS: N/A
NON-U.S. MANUFACTURING LOCATIONS: N/A
Our Products
Kitemetrics
Keyword level attribution for Apple Search Ads. Optimize your bids and increase your revenue. Sign up for free at kitemetrics.com.
White Noise and Deep Sleep Sounds
Calming and relaxing sounds that will help you sleep like a baby tonight.
Download for free from the App Store.
Get it on Google Play.
Our Sponsors
Get Sleepy

The free podcast that puts you to sleep with meditative bedtime stories. Listen at getsleepy.com.